In the rapidly evolving landscape of software development, the transition from DevOps to DevSecOps has emerged as a strategic imperative. While DevOps has proven instrumental in fostering collaboration between development and operations teams, the integration of security into this paradigm becomes paramount to address the escalating challenges posed by cyber threats and compliance requirements.
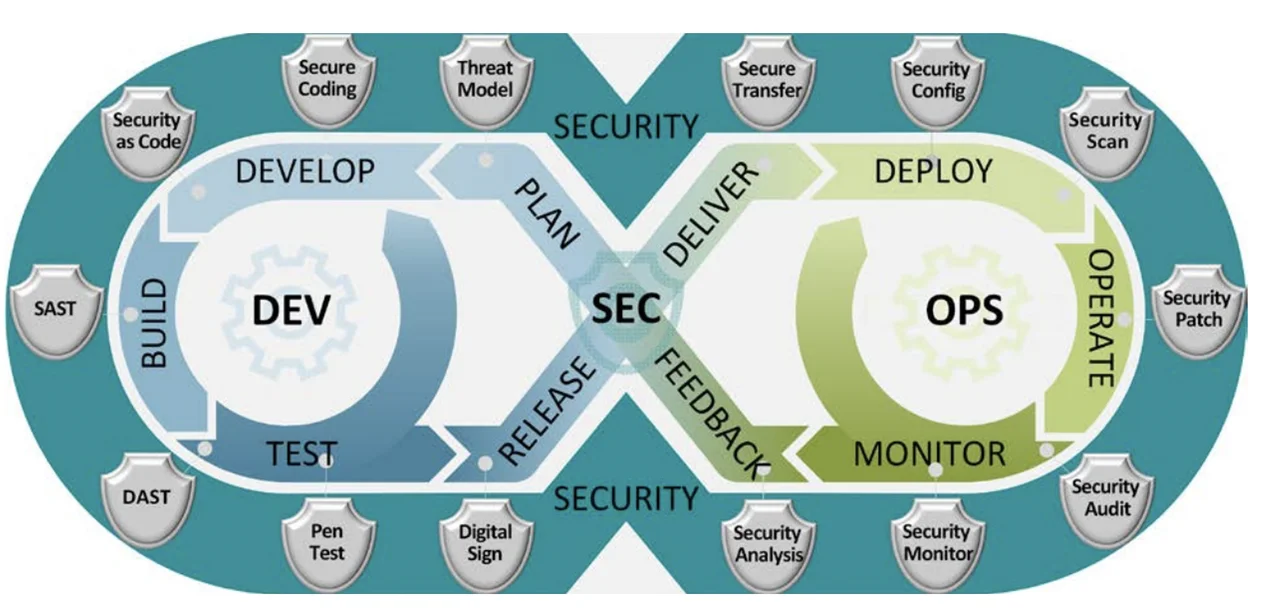
DevSecOps Lifecycle (from DoD Enterprise DevSecOps Reference Design, Version 1.0, 12 August 2019)
Building a Security Culture: Foster a culture of shared responsibility where security is everyone's concern. This involves educating and training development, security, and operations teams on security best practices.
Collaborative Communication: Encourage open communication and collaboration between teams. This can be achieved through regular meetings, joint workshops, and cross-functional training sessions.
Automated Security Testing: Embed security testing tools and practices into the continuous integration and continuous deployment (CI/CD) pipelines. This includes static application security testing (SAST), dynamic application security testing (DAST), and dependency scanning.
Shift Left Security: Identify and address security vulnerabilities early in the development process. Shift security testing to the left, meaning it occurs as early as possible in the development lifecycle.
Automated Compliance Checks: Apply security policies and compliance standards through automated tools to ensure that infrastructure configurations adhere to security best practices.
Continuous Monitoring: Implement continuous monitoring of infrastructure components to detect and remediate security issues promptly.
Identifying and Training Champions: Designate individuals within development and operations teams as security champions. These champions serve as advocates for security best practices and help disseminate security knowledge within their respective teams.
Empowering Teams: Equip security champions with the necessary tools and resources to empower them to make security-conscious decisions during the development process.
Automated Incident Response: Develop automated incident response processes to detect and respond to security incidents swiftly.
Collaborative Incident Resolution: Foster collaboration between development, security, and operations teams during incident response to ensure a unified and efficient resolution.
Feedback Loops: Establish feedback loops to continuously improve security practices based on lessons learned from incidents, security assessments, and regular retrospectives.
Metrics and Key Performance Indicators (KPIs): Define and track security-related metrics and KPIs to measure the effectiveness of DevSecOps practices and identify areas for improvement.
Implementing DevSecOps is a multifaceted journey that requires commitment, collaboration, and continuous improvement. By fostering a security-centric culture, integrating security practices into development workflows, and embracing automation, organizations can achieve the dual goals of accelerated development and enhanced security. DevSecOps is not just a set of practices; it is a mindset that encourages the alignment of development, security, and operations teams towards a common goal of building secure and resilient software.